Phishing for answers: Point Park students bewildered as inboxes bombarded with malicious emails, links
Analysis shows phishing emails carry tell-tale signs of being not trustworthy for students, wider campus community
September 29, 2021
On Monday morning, students awoke to an email from a fellow student titled “CAREER IN POINT PARK !!!,” which offered recipients several potential job opportunities with a link to apply. Although this may at first seem like a fantastic opportunity full of potential, most students knew better. This email was just the latest in an onslaught of phishing messages distributed to the student body.
Point Park students have been experiencing an influx of phishing messages sent to their school-affiliated email addresses within the first few weeks of the semester. With dozens of phishing scams still being sent to people’s inboxes, students are left wondering if an end to the phishing bombardment is in sight.
Phishing messages, scam emails disguised as genuine messages from trustworthy sources, have risen as a security threat in the age of the internet. These messages usually contain links or other information instructing users to complete tasks under the guise of an important cause or issue that needs to be addressed (such as a problem with a financial account or security). However, the actual contents of these messages are entirely false, serving only to trick users into giving away valuable information or access to their account.
Lately, the university has become the victim of a series of phishing attacks. The scam messages have come in a variety of forms, including some that appeared to come from the IT Department. These messages were designed to gain personal identification information (PII).
Subsequent messages also used compromised Point Park student email addresses, using them to send phishing messages to other students. Tim Wilson, IT Director at Point Park, explained how this might have happened.
“These past few phishing attempts have originated from actual Point Park accounts where the password has been compromised,” Wilson said. “We are thinking this has been through a combination of weak passwords, other phishing attacks, and possibly malware to capture a password. Be very vigilant installing apps on your devices. Sometimes these can install Malware to capture passwords and other types of Personally Identifiable Data.”
Although the exact methods used to take over accounts are uncertain, it is possible that information collected by scammers through these phishing messages has been used in other scams. By sending messages from Point Park student addresses, scammers can make the emails seem more legitimate than if they were to come from a source outside of the university.
On Sept. 13, students received the following email:
Hi
I’m offering a remote part-time personal assistant position that pays $500 weekly, several attempts to email you but it keeps bouncing back, kindly provide an alternative email when replying this email and more details will be provided.
This message, sent from the actual email address of a Point Park student, provides an enticing job offer to get students’ attention. However, the sender said that they are having difficulty with sending the email, asking students to provide a separate, personal address instead. Although this may seem like a genuine offer from a fellow student on the surface, it is actually a carefully constructed message meant to draw out specific information in response.
This message in particular is signed with a name that does not match that of the address sending the message, a hint that this message is not actually legitimate. As Wilson explains, there are ways to detect scam messages before it is too late.
“The best defense is to be smart about what you click on,” Wilson said. “As always, these types of efforts are becoming more and more sophisticated. As a side note, many of them are not just using email as a vehicle either. Many hacking operations are even using text messages as a way to get you to click on things. Humans are the best means of defense.”
Wilson also stated that no personal identification information was compromised in the phishing attack, though later admitted that student email addresses were compromised. Furthermore, Wilson said he suspects that the sender or senders of the messages found student email addresses by referencing the school’s account naming conventions and also said he does not believe that Point Park was targeted specifically, despite the widespread delivery of the messages.
Although many students were recipients of scam messages, some were hit harder than others. Junior SAEM Major Frankie Bracey was bombarded by a barrage of phishing messages, at one point receiving one every two minutes.
“I find it annoying how easy it is for people to get into the IT system and do this,” Bracey said. “I’ve had four inside of 8 minutes. They need a better security system.”
Wilson explained that Point Park’s current security system has checks in place to protect the university from spam.
“We have spam tools running as part of our Microsoft O365 environment,” Wilson said. “They are not 100% foolproof though, as you can see from this attack.”
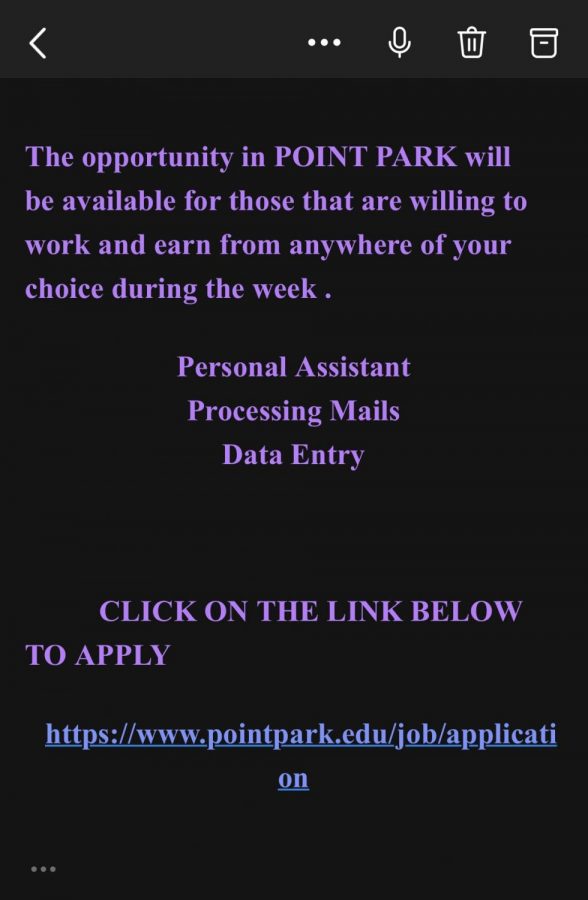
As Wilson explains, Point Park’s spam detection tools are not perfect, which was further demonstrated by more messages as recently as Monday, Sept. 27. The most recent message, titled “CAREER IN POINT PARK !!!,” advertises that, “The opportunity in POINT PARK will be available for those that are willing to work and earn from anywhere of your choice during the week.” This message, which also comes from an actual student’s email address, also includes a link that appears to lead to a page on Point Park’s website. However, inspecting the link reveals that it actually leads to a Google Form. The IT Department has confirmed this email is a phishing message.
Another recent message from Sunday, titled “URGENT APPROVAL IS REQUIRED !!!,” asks the recipient to follow a link to “sign in with (their) EDU EMAIL to view the document for a kind and urgent consideration.” This particular example tries to pressure students into providing their login information under the impression that they are signing into a trustworthy site.
By comparing these emails, a few similarities can be observed. Both messages use fully capitalized titles that end with three exclamation marks (which are also separated from the rest of the text by a space). Furthemore, the messages are both very short at under 40 words each and contain a disguised link.
Looking for specific characteristics such as poor grammar, vague subjects, and, most importantly, suspicious links can help students detect malicious messages in the future. Of course, students can also always send emails they are uncertain of to the IT Help Desk to verify their authenticity.
For now, the source of the messages remains unknown, making it difficult to take measures in response. As a result, it is up to students to stay alert to avoid falling for these scams, according to Wilson.
“Educate yourself. If you don’t know who it is from, don’t click on it. You may always report suspicious email messages to our Help Desk for further analysis,” he said. “Just as with the ‘see something, say something’ campaign for terrorism type activities – the same can be said for socially engineered email threats.”